Hash Cracking Crash Course
Archit ChoudharyThere was a time when passwords were stored in plaintext on servers where people made accounts. This was a time many hackers reminisce about. This was also a time where TLS/SSL did not exist and HTTP requests (which are used to authenticate user credentials on the web) were sent completely unencrypted, making it an amateur task to capture someone's passwords, credit card numbers, emails, and basically everything else private to them.
Fortunately, we have moved on as a species. Now when you capture a POST request going from a user's computer to the web server to authenticate him, you see an entirely unreadable blob of text. It's called a hash.
In this tutorial series, you will learn how to crack such hashes and retrieve passwords and other valuable information.
Join our Discord using this invite link to be a part of the SHACK community.
What's a Hash?
A hash function is a mathematical function taking an input of arbitrary length (a string, a file, a collection of multiple files, etc.) and producing an output of fixed length (32 bytes, 64 bytes, etc.) When encrypting sensitive information, we use a special subset of such functions called cryptographic hash functions satisfying some extra properties listed here. The term "hash function" from this point will only refer to this subset.
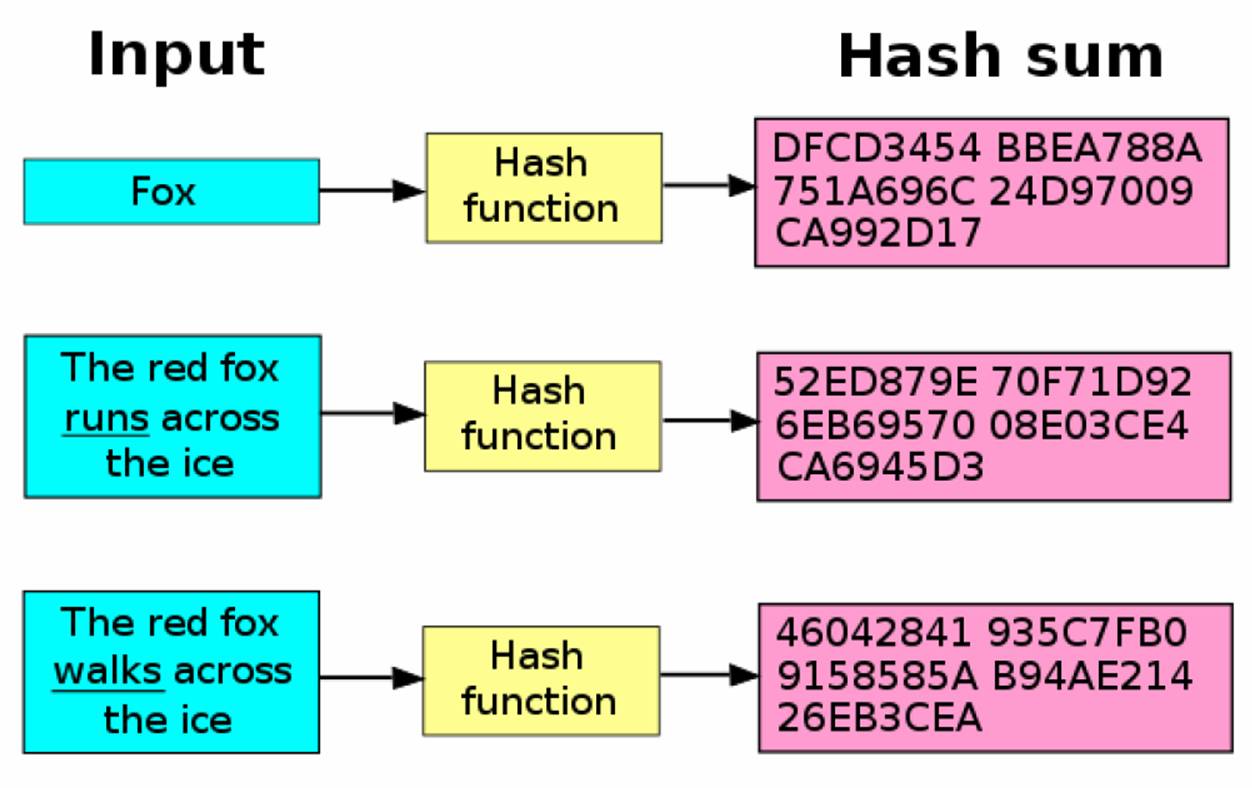
By applying a hash function to sensitive data, the attacker is now required to undo (or crack) the hash. This is very hard and often impossible. But sometimes, with weak passwords and several GPUs, it's feasible.
Quick note: When a user registers an account with a certain password, the server hashes the password and stores the hash in the database. When the user requests access and enters their password, the server hashes this given password and compares this hash with the one in the database.
Salted Hashes
An important concept is salting. If I register an account online with the password "testing123" (don't do this, for the love of all that is holy), the server will stick a random string at the end (called a salt), making the string "testing123@#8udi1*&/", and only then apply the hash. This makes the password longer and harder to crack.

The database stores the hashed password and the random salt. When a user wants access, the server adds the salt to the user-provided password, hashes it, and compares this hash with the one in the database.
How Do You Crack a Hash?
There are a whole host of ways to crack hashes:
- Rainbow tables
- Brute force and mask attacks (targeted brute force)
- Dictionary attacks
- Hybrid (brute force + dictionary) attacks
- Rule-based attacks
Throughout this series, we'll look at each one of these. The program we will use is hashcat, so it would be a smart idea to install it now. You can get the binaries (and the source code) from the official Hashcat website if it's not in your apt repositories.
See you in the next tutorial on rainbow tables!
Join our Discord using this invite link to be a part of the SHACK community.
